OpenConfig with PAN-OS - Part 1

In this post we are looking on how to gather telemetry data from Palo Alto firewalls via the PAN-OS OpenConfig plugin. In the upcoming part 2, we will take a look on how to configure (for example for automation purposes) the firewall via the OpenConfig.
Prerequisites
- Firewall must be running PAN-OS version 10.1 or higher for the OpenConfig plugin to be available for install
- Install the OpenConfig plugin (in this guide, and part 2 as well, we are using version 1.3)
Note: Please note that (based on my testing) for you to be able to use OpenConfig plugin version 2.0 you must be running PAN-OS version of at least 11.0. I noticed that you can install the version 2.0 on lesser version firewalls but it will not start nor function.
I'm running the OpenConfig plugin on VM-series firewall, so your mileage may vary when running this on hardware (considering the comment below).
I have noticed that you might run into weird Out-Of-Memory (OOM) conditions running the plugin (at least versions from 1.0 to 1.3). It seems that these were resolved by giving the VM more memory (I'm running 2 vCPU FLEX licensed model with 16gb of RAM).
Palo Alto has quite good documentation on the supported models as well, please check them out here: https://docs.paloaltonetworks.com/openconfig/1-3/openconfig-admin/openconfig-models
Installing the plugin
From the PAN-OS GUI, navigate to Device -> Plugins and install the desired version (in this guide openconfig-1.3.0).
After installation and commit you will see the OpenConfig config tree available in the Device page. And when the plugin starts and works properly you see the following output.
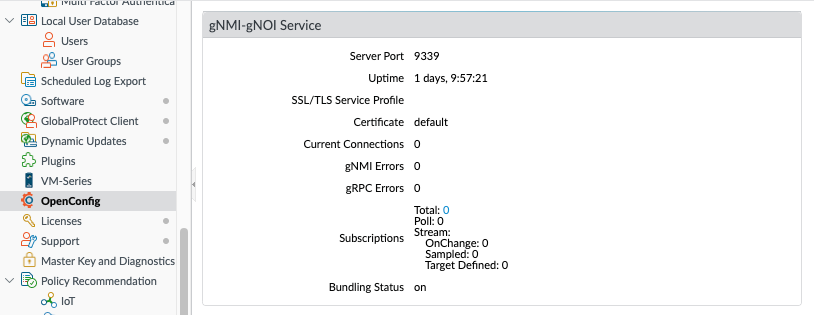
Using OpenConfig with gNMIC OpenConfig client
Verify functionality by checking PAN-OS firewall OpenConfig capabilities.
# gnmic -a 10.10.10.1:9339 -u testuser -p testpassword --skip-verify -e json_ietf capabilities
gNMI version: 0.7.0
supported models:
- openconfig-relayagent, OpenConfig working group, 1.1.0
- pan-relay-agent-devs, Palo Alto Networks, 0.0.1
- openconfig-zones, OpenConfig working group, 1.1.0
- openconfig-interfaces, OpenConfig working group, 2.4.3
- openconfig-vlan, OpenConfig working group, 3.2.0
- openconfig-if-ethernet, OpenConfig working group, 2.8.1
- openconfig-if-ip, OpenConfig working group, 3.0.0
- openconfig-if-aggregate, OpenConfig working group, 2.4.3
- openconfig-if-tunnel, OpenConfig working group, 0.1.1
- pan-if-deviations, OpenConfig working group, 1.0.0
- openconfig-local-routing, OpenConfig working group, 1.1.0
- openconfig-components, OpenConfig working group, 1.1.0
- pan-plat-devs, Palo Alto Networks, 0.0.1
- openconfig-lldp, OpenConfig working group, 1.1.0
- pan-lldp-devs, Palo Alto Networks, 0.0.1
- openconfig-routing-policy, OpenConfig working group, 1.1.0
- pan-routing-policy-devs, Palo Alto Networks, 0.0.1
- openconfig-bfd, OpenConfig working group, 1.1.0
- pan-bfd-devs, Palo Alto Networks, 0.0.1
- openconfig-hagroups, OpenConfig working group, 1.1.0
- pan-high-availability-devs, Palo Alto Networks, 0.0.1
- openconfig-bgp, OpenConfig working group, 6.0.0
- openconfig-rib-bgp, OpenConfig working group, 0.7.0
- pan-bgp-deviations, Palo Alto Networks, 0.0.1
- openconfig-lacp, OpenConfig working group, 1.1.0
- pan-lacp-devs, Palo Alto Networks, 0.0.1
- openconfig-network-instances, OpenConfig working group, 1.1.0
- pan-network-instance-devs, Palo Alto Networks, 0.0.1
- pan-ospfv2-devs, Palo Alto Networks, 0.0.1
- openconfig-system, OpenConfig working group, 0.9.1
supported encodings:
- JSON_IETF
Some introductory use cases
You can use gNMIC OpenConfig client to try out the get and subscribe commands. Later in the post I will show how to gather the data using Telegraf. In the example below we are getting status of interface ethernet1/1. You can use name=* to get all interfaces.
# gnmic -a 10.10.10.1:9339 -u testuser -p testpassword --skip-verify -e json_ietf get --path /interfaces/interface[name=ethernet1/1]/state/oper-status
[
{
"source": "10.10.10.1:9339",
"timestamp": 1703755312952484322,
"time": "2023-12-28T09:21:52.952484322Z",
"updates": [
{
"Path": "interfaces/interface[name=ethernet1/1]/state/oper-status",
"values": {
"interfaces/interface/state/oper-status": "UP"
}
}
]
}
]
You can use the example above to get status of all the interfaces. But in the example below we are subscribing for changes in the interface status (--mode stream and --stream-mode on_change). This could be used in monitoring interface status changes in real time. When the interface goes down, you get immediate output from the firewall regarding the change in interface status. This can be used for monitoring other states as well (that are available in the PAN-OS supported OpenConfig models).
# gnmic -a 10.10.10.1:9339 -u testuser -p testpassword --skip-verify -e json_ietf sub --path /interfaces/interface[name=ethernet1/5]/state/oper-status --mode stream --stream-mode on_change
!! {"name":"default-1703755482","paths":["/interfaces/interface[name=ethernet1/5]/state/oper-status"],"mode":"stream"}
{
"source": "10.10.10.1:9339",
"subscription-name": "default-1703755482",
"timestamp": 1703755482000000000,
"time": "2023-12-28T09:24:42Z",
"updates": [
{
"Path": "interfaces/interface[name=ethernet1/5]/state/oper-status",
"values": {
"interfaces/interface/state/oper-status": "UP"
}
}
]
}
{
"source": "10.10.10.1:9339",
"subscription-name": "default-1703755482",
"timestamp": 1703755529000000000,
"time": "2023-12-28T09:25:29Z",
"updates": [
{
"Path": "interfaces/interface[name=ethernet1/5]/state/oper-status",
"values": {
"interfaces/interface/state/oper-status": "DOWN"
}
}
]
}
Gather streaming interface statistics every 10 second intervals. This will subscribe to (specific or all) interface metrics from the firewall to be submitted every 30 second intervals. This way you can get much more detailed statistics than using, for example, SNMP queries.
# gnmic -a 10.10.10.1:9339 -u testuser -p testpassword --skip-verify -e json_ietf sub --path /interfaces/interface[name=ethernet1/1]/state/counters --mode stream --stream-mode sample --sample-interval 30s
!! {"name":"default-1703761235","paths":["/interfaces/interface[name=ethernet1/1]/state/counters"],"mode":"stream"}
{
"source": "10.10.10.1:9339",
"subscription-name": "default-1703761235",
"timestamp": 1703761235000000000,
"time": "2023-12-28T11:00:35Z",
"updates": [
{
"Path": "interfaces/interface[name=ethernet1/1]/state/counters/in-octets",
"values": {
"interfaces/interface/state/counters/in-octets": 6729602137
}
},
{
"Path": "interfaces/interface[name=ethernet1/1]/state/counters/in-pkts",
"values": {
"interfaces/interface/state/counters/in-pkts": 107598062
}
},
{
"Path": "interfaces/interface[name=ethernet1/1]/state/counters/in-unicast-pkts",
"values": {
"interfaces/interface/state/counters/in-unicast-pkts": 107598001
}
},
...
Using Telegraf for OpenConfig telemetry
Using the following Telegraf inputs you can gather the data as in examples above. I'm using sample and on_change in the Telegraf examples below.
Note: I'm not showing other Telegraf config here. You can configure the outputs (for example InfluxDB, Kafka, Splunk etc.), intervals and other features by looking at examples available online.
# Define the GNMI input plugin
[[inputs.gnmi]]
addresses = ["10.10.10.1:9339"]
username = "testuser"
password = "testpassword"
# Set encoding as "json_ietf"
encoding = "json_ietf"
# And as I'm using self-signed certificate, I'm enabling TLS but ignoring the certificate check.
enable_tls = true
insecure_skip_verify = true
# Define GNMI subscription (when any of the interface statuses change)
[[inputs.gnmi.subscription]]
name = "ifstatus_gnmi"
origin = "openconfig-interfaces"
path = "/interfaces/interface/state/oper-status"
subscription_mode = "on_change"
# Define GNMI subscription (gather all interface counters at 30sec intervals)
[[inputs.gnmi.subscription]]
name = "ifcounters_gnmi"
origin = "openconfig-interfaces"
path = "/interfaces/interface/state/counters"
subscription_mode = "sample"
sample_interval = "30s"
Conclusion
This post should get you started with the telemetry part of OpenConfig implementation on PAN-OS firewalls. The OpenConfig support is by NO MEANS all inclusive (and is actually missing quite a lot of features), but you still can get a lot of metrics for monitoring purposes. OpenConfig implementation is rather new for PAN-OS so we still have to wait full blown implementation. In part 2 we will be looking into how to configure firewalls using the OpenConfig plugin.